Innkeeper
Introduction
Innkeeper p rovides FTP and HTTP access to host maven artifacts for ApiOmat Microservices. One repository per service and system is available. User authentication is handled by Innkeeper using either YAMBAS module/system authorization.
|
HTTP port |
2400 |
|
Context path |
/hosting |
|
Host |
Component interactions
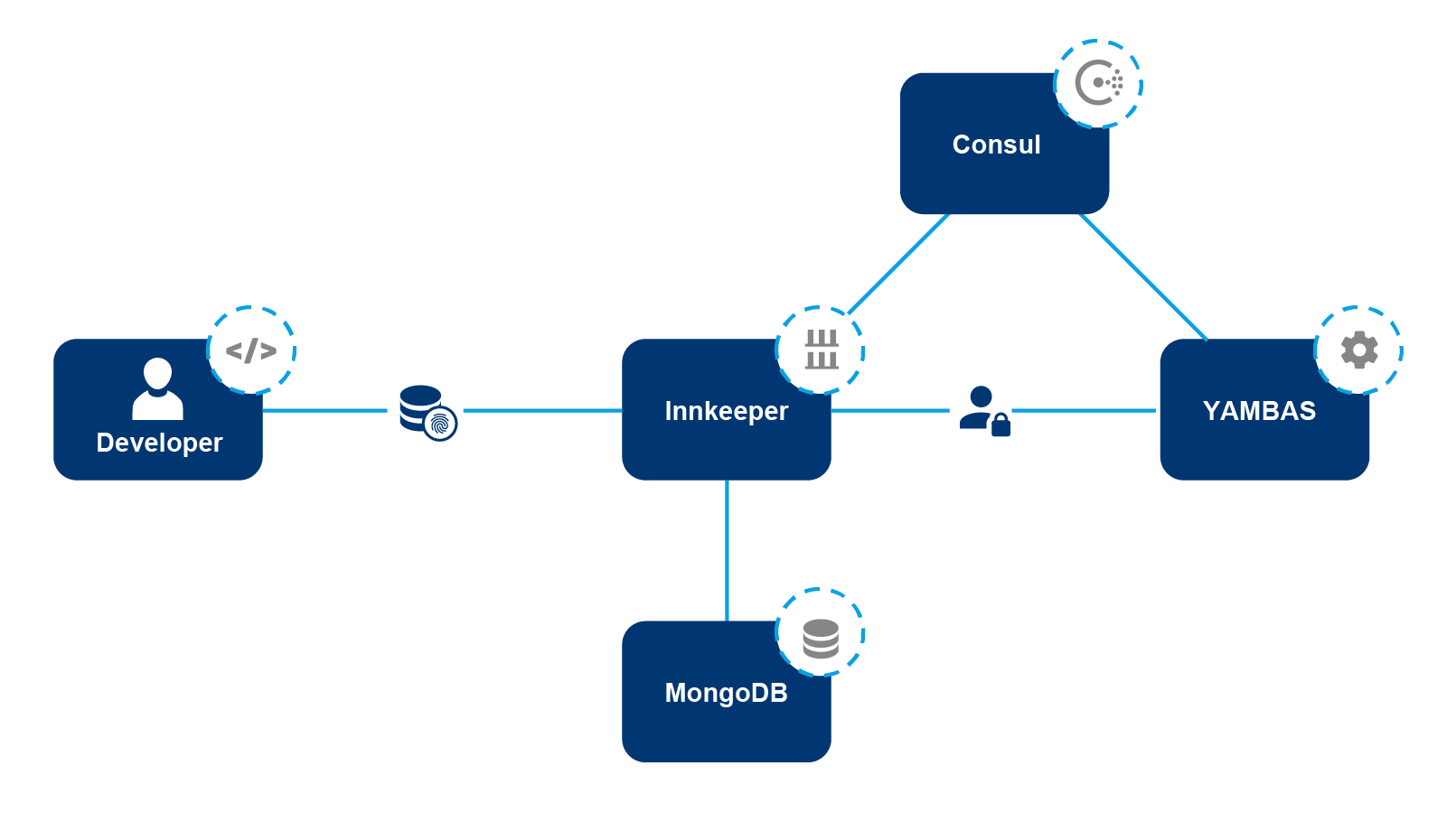
The above diagram represents interactions between actors and components where Innkeeper is involved within the ApiOmat cloud. In this diagram you can see the developer as an actor, the two services Innkeeper and YAMBAS as components, the discovery service Consul and the database MongoDB. Each service interacts with the Consul discovery to register itself, additionally Innkeeper uses Consul to retrieve information to communicate with YAMBAS.
At the upper level you have the developer interaction with Innkeeper. A developer can ask Innkeeper to store any kind of file under a specific path and delete one or multiple files under a specific path. Every operation is authenticated using ApiOmat credentials.
Innkeeper is interacting with YAMBAS to check for the developer rights over modules/system. Innkeeper also uses YAMBAS to get information about modules available to the authenticated user. Lastly Innkeeper can also notify YAMBAS when a generated service archive is pushed so the meta data information of the services will be kept up to date.
Innkeeper uses MongoDB or Filesystem (since 2.2.0) to store and retrieve the files provided by the developer.
Usage
Deploy a project artifact to Innkeeper
Add the repository to the pom.xml of your project to connect it to the Innkeeper (in this example the LIVE repository):
...<distributionManagement> <repository> <id>aomrepo</id> <name>Releases</name> <url>http://localhost:2400/maven2/LIVE</url> </repository> <snapshotRepository> <id>aomrepo-snapshots</id> <name>Snapshot</name> <url>http://localhost:2400/maven2-snapshots/LIVE</url> </snapshotRepository> </distributionManagement>...Set up account credentials in ~/.m2/settings.xml :
<settings> <servers> <server> <id>aomrepo</id> <username>{APIOMAT_USER_NAME}</username> <password>{APIOMAT_USER_PASSWORD}</password> </server> </servers></settings>(to avoid storing your password as plain text into the settings.xml you can use the following guide https://blog.sonatype.com/2009/10/maven-tips-and-tricks-encrypting-passwords/ )
Deploy the project to the Innkeeper repo :
The Service needs com.apiomat.microservice set as Maven groupId to be deployed to either maven2 or maven2-snapshots, the project name should also correspond to the ApiOmat available/wanted service name.
mvn deployUse an artifact from Innkeeper in a project
Use in other pom.xml :
...<repositories> <repository> <id>aomrepo</id> <url>http://localhost:2400/hosting/maven2/LIVE</url> </repository></repositories>...